MongoDB Ransomware Protection: Secure Your Database with These Essential Strategies
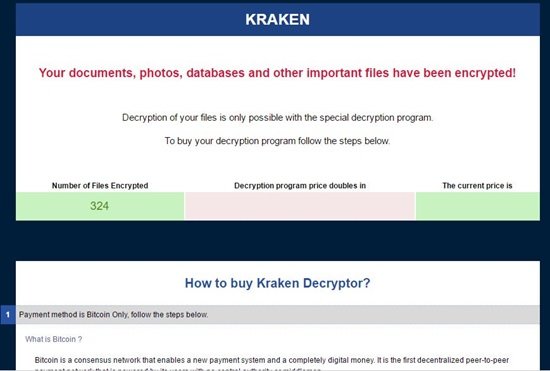
Unsecured MongoDB installations have recently become targets of ransomware attacks, resulting in data being held hostage. This article will delve into the fundamentals of MongoDB and explore crucial strategies to fortify and safeguard your database against such threats. Ensuring robust security measures is paramount in today’s digital landscape to protect sensitive information and maintain operational integrity. Understanding the vulnerabilities and implementing proactive defenses are key to mitigating the risk of ransomware attacks on your MongoDB deployments.
What is MongoDB¶
MongoDB stands out as an open-source database solution that employs a flexible document data model for storing information. Unlike traditional databases that rely on rigid tables and rows, MongoDB utilizes an architecture based on collections and documents. This approach offers greater agility and scalability in managing diverse data types.
The dynamic schema design of MongoDB allows documents within a single collection to possess varying fields and structures. This flexibility is particularly advantageous for applications dealing with evolving data requirements. MongoDB leverages BSON, a binary representation of JSON-like documents, as its document storage and data interchange format. This binary format enhances data integration speed and efficiency for specific application types, making it a popular choice for modern development projects.
Ransomware Attacks on MongoDB Data¶
A series of ransomware attacks have targeted MongoDB installations that were not adequately secured, highlighting a significant cybersecurity concern. These incidents underscore the importance of proper security configurations for database systems exposed to the internet. Failure to implement necessary safeguards can leave sensitive data vulnerable to malicious actors seeking financial gain through data encryption and ransom demands.
Several years ago, security expert Victor Gevers uncovered approximately 200 MongoDB installations compromised by ransomware. Subsequently, the number of affected databases surged to 2000, as reported by Shodan founder John Matherly. Initial reports indicated that attackers were demanding a ransom of 1 Bitcoin in exchange for the decryption key. This widespread attack served as a stark reminder of the potential consequences of neglecting database security.
Unfortunately, this trend has continued, with more hackers exploiting poorly configured databases to access, copy, and delete data for ransom. The ease with which attackers can identify and compromise unsecured MongoDB instances emphasizes the need for proactive security measures and continuous monitoring. Organizations must prioritize database security to prevent data breaches and the associated financial and reputational damage.
How MongoDB Ransomware Sneaks In¶
The primary vulnerability exploited in MongoDB ransomware attacks is the accessibility of servers over the internet without password protection. Hackers specifically target MongoDB servers that are exposed to the public internet and lack basic authentication measures. Server administrators who operate their MongoDB instances without setting up a password and continue using default usernames inadvertently create an open invitation for cybercriminals.
Adding to the problem, instances of servers being re-hacked by different ransomware groups have emerged. These groups replace existing ransom notes with their own, creating a chaotic situation where victims are unsure of whom to pay, or even if paying will result in data recovery. This secondary exploitation further reduces the likelihood of data retrieval, even if the ransom is paid. Therefore, there is no guarantee that stolen data will be returned, and paying the ransom may still result in permanent data loss. This grim reality emphasizes the critical need for preventative security measures rather than relying on post-attack solutions.
MongoDB Security¶
Implementing robust security measures is not merely an option but an absolute necessity for MongoDB deployments. Server administrators must prioritize assigning strong, unique passwords and usernames for database access. This fundamental step prevents unauthorized entry and forms the first line of defense against potential attackers.
Companies that are using default MongoDB installations are strongly advised to take immediate action. This includes updating their MongoDB software to the latest version, which often includes critical security patches. Setting up proper authentication mechanisms is also crucial to verify user identities before granting access. Furthermore, locking down port 27017, the default MongoDB port that has been frequently targeted by hackers, is essential to reduce the attack surface and prevent unauthorized connections. These proactive steps significantly enhance the security posture of MongoDB databases and minimize the risk of ransomware and other cyber threats.
Steps to Protect Your MongoDB Data¶
Securing your MongoDB data requires a multi-faceted approach, incorporating several key security measures. By implementing these strategies, you can significantly reduce the risk of ransomware attacks and protect your valuable data assets.
1. Enforce Access Control and Authentication¶
The first and most critical step is to enforce strict access control and authentication for your MongoDB server. Enabling access control ensures that only authorized users can connect to your database. Specify a robust authentication mechanism that requires all users to present valid credentials before granting access. This prevents anonymous or unauthorized connections, which are often the entry point for attackers.
MongoDB 3.4 and later versions offer the capability to configure authentication on an unprotected system without requiring downtime. This feature allows for seamless integration of security measures into existing deployments without disrupting operations. Implementing strong authentication is the cornerstone of MongoDB security and should be prioritized in every deployment.
2. Setup Role-Based Access Control¶
Moving beyond basic authentication, implement Role-Based Access Control (RBAC) to manage user permissions effectively. RBAC allows you to define roles that specify precise access levels for different users, adhering to the principle of least privilege. Instead of granting full administrative access, create roles tailored to specific job functions, granting only the necessary permissions for each role.
For example, you might create a “read-only” role for users who only need to query data, and a “developer” role with permissions to modify data schemas and indexes. By assigning users to roles that match their responsibilities, you minimize the potential damage from compromised accounts and ensure that users only have access to the resources they need. This granular control over access significantly enhances database security.
3. Encrypt Communication¶
Encryption is paramount for protecting data in transit and at rest. Configure MongoDB to use TLS/SSL encryption for all incoming and outgoing connections. TLS/SSL encrypts the communication channel between MongoDB clients (mongod and mongos components) and applications, making it extremely difficult for attackers to intercept and decipher data transmitted over the network.
For data at rest, consider using MongoDB Enterprise 3.2 or later, which offers WiredTiger storage engine’s native Encryption at Rest. This feature encrypts data at the storage layer, providing an additional layer of security against physical theft or unauthorized access to storage media. If you are not using WiredTiger’s encryption, ensure that MongoDB data is encrypted on each host using file-system, device, or physical encryption methods. Employing robust encryption strategies safeguards sensitive data from unauthorized access, both during transmission and storage.
4. Limit Network Exposure¶
Minimizing network exposure is crucial for reducing the attack surface of your MongoDB deployment. Ensure that your MongoDB instances run within a trusted network environment, ideally behind a firewall. Restrict access to MongoDB network interfaces and ports to only trusted clients and applications. Avoid exposing MongoDB directly to the public internet whenever possible.
Implement firewall rules to control inbound and outbound traffic, allowing only necessary connections to port 27017 (or your configured MongoDB port). Consider using a Virtual Private Network (VPN) to further secure access, especially for remote administrators. By limiting network exposure, you significantly reduce the avenues through which attackers can attempt to compromise your database.
5. Backup Your Data¶
Regular data backups are essential for disaster recovery and business continuity. Implement a robust backup strategy for your MongoDB data, ensuring that backups are performed frequently and stored securely in a separate location. In the event of a ransomware attack or data loss incident, backups provide a means to restore your database to a known good state, minimizing downtime and data loss.
MongoDB Cloud Manager and MongoDB Ops Manager offer continuous backup solutions with point-in-time recovery capabilities. These tools simplify backup management and provide features like automated backups, monitoring, and alerting. Furthermore, Cloud Manager can be configured to detect if your MongoDB deployment is exposed to the internet, providing proactive security monitoring. Regular backups are a critical component of a comprehensive MongoDB security strategy.
6. Audit System Activity¶
Regular auditing of system activity is vital for detecting and responding to security incidents. Implement MongoDB’s auditing facility, available in MongoDB Enterprise, to record system events on your MongoDB instances. Track access to database configurations, user authentication attempts, and data modification operations.
Analyze audit logs periodically to identify any irregular or suspicious activities, such as unauthorized access attempts, data exfiltration, or unexpected changes to database configurations. Auditing provides valuable insights into database activity and helps in identifying and responding to security breaches in a timely manner. Proactive log monitoring and analysis can significantly enhance your security posture and incident response capabilities.
7. Run MongoDB with a Dedicated User¶
For enhanced security, run MongoDB processes using a dedicated operating system user account. Create a specific user account solely for running MongoDB services and grant it only the necessary permissions to access data and resources. This principle of least privilege extends to the operating system level, reducing the potential impact of a compromised MongoDB process.
Ensure that the dedicated MongoDB user account does not have unnecessary permissions, such as administrative privileges or access to sensitive system files. Isolating MongoDB processes under a dedicated user account limits the potential damage if the MongoDB process is compromised and helps contain security breaches.
8. Run MongoDB with Secure Configuration Options¶
MongoDB offers several configuration options that can enhance security. Disable server-side scripting if you do not utilize operations like mapReduce, group, and $where that execute JavaScript code on the server. The --noscripting command-line option can be used to disable server-side scripting, reducing the attack surface by preventing the execution of potentially malicious JavaScript code.
Ensure that input validation is enabled. MongoDB enables input validation by default through the wireObjectCheck setting. This setting verifies that all documents stored by the mongod instance are valid BSON, preventing injection attacks and data corruption. Utilize only the MongoDB wire protocol on production deployments and maintain input validation enabled for optimal security.
9. Request a Security Technical Implementation Guide (where applicable)¶
For deployments within the United States Department of Defense or organizations requiring STIG compliance, request the Security Technical Implementation Guide (STIG) from MongoDB Inc. The STIG provides detailed security guidelines and configuration recommendations specifically tailored to MongoDB deployments in sensitive environments.
While primarily intended for DoD environments, the STIG can also serve as a valuable resource for organizations in other sectors seeking to implement robust security measures. Contact MongoDB Inc. to request a copy of the STIG and leverage its guidance to enhance your MongoDB security posture, especially if compliance with security standards is a requirement.
10. Consider Security Standards Compliance¶
For applications requiring compliance with industry security standards such as HIPAA or PCI-DSS, consult the MongoDB Security Reference Architecture. This document provides detailed guidance on how to leverage MongoDB’s security capabilities to build compliant application infrastructure. Understanding and adhering to relevant security standards is crucial for organizations operating in regulated industries.
The MongoDB Security Reference Architecture outlines the key security controls and configurations necessary to meet the requirements of HIPAA, PCI-DSS, and other compliance frameworks. By aligning your MongoDB deployment with these standards, you ensure that your application infrastructure meets industry best practices and regulatory obligations, minimizing security risks and demonstrating due diligence.
How to Find Out if Your MongoDB Installation is Hacked¶
Detecting a MongoDB ransomware attack promptly is crucial for mitigating damage and initiating recovery procedures. Be vigilant for the following signs that may indicate a compromise:
-
Verify your databases and collections. Ransomware attackers often drop existing databases and collections, replacing them with a new database containing a ransom note. Check your MongoDB instance for any unexpected databases or collections, particularly those with names indicating ransom demands. The absence of expected databases or the presence of unfamiliar ones should raise immediate alarm.
-
If access control is enabled, audit the system logs. Examine system logs for unauthorized access attempts or suspicious activity. Look for commands that indicate data manipulation, such as commands that dropped databases or collections, modified user accounts, or created ransom demand records. Audit logs provide a historical record of database activity and can reveal evidence of malicious actions. Regularly reviewing audit logs is essential for proactive threat detection.
It’s important to remember that even if you pay the ransom, data recovery is not guaranteed. Therefore, your primary focus after detecting an attack should be securing your MongoDB cluster to prevent further unauthorized access and data breaches. Implement the security measures outlined in this article to fortify your defenses and minimize the risk of future attacks.
How do I Protect My MongoDB Database?¶
Protecting your MongoDB database involves implementing a comprehensive set of security practices. As discussed in this article, key strategies include enforcing access control and authentication, configuring role-based access control, encrypting communications, limiting network exposure, and regularly backing up your data. These measures collectively create a robust security posture for your MongoDB deployments.
Beyond these core strategies, continuous monitoring, regular security audits, and staying updated with the latest security patches are also crucial. Proactive security management, coupled with a strong understanding of potential threats and vulnerabilities, is essential for maintaining the confidentiality, integrity, and availability of your MongoDB data.
Is MongoDB a Secure Database?¶
Yes, MongoDB is inherently a secure database platform suitable for a wide range of applications. It offers a comprehensive set of security features and capabilities that, when properly configured and implemented, can provide a robust security posture. MongoDB is a viable alternative to other database solutions like Apache Cassandra, DynamoDB, and Redis, offering comparable security features and performance.
The security of any database, including MongoDB, ultimately depends on how it is deployed and managed. By diligently implementing the recommended security best practices, organizations can leverage MongoDB’s security features to effectively protect their data assets. MongoDB’s security capabilities, combined with proactive security management, make it a secure and reliable database choice for modern applications.
What security measures do you find most critical for protecting your MongoDB databases? Share your thoughts and experiences in the comments below!
Post a Comment