Privacy Check: See Which Apps Access Your Google Account & Secure Your Data
It’s a common convenience to use your Google account to sign in to various websites and applications. This streamlined approach simplifies the login process, allowing you to bypass the need to create and remember countless usernames and passwords for different online services. Google acts as a trusted intermediary, facilitating the sharing of specific information from your Google Account with these third-party platforms. This sharing occurs without exposing your primary login credentials, such as your username and password, directly to these external sites.
The information shared through your Google Account typically includes basic details necessary for service functionality and personalization. This may encompass:
- Email address: Used for communication and account identification.
- Name: For personalizing the user experience within the application or website.
- Country and language: To tailor content and settings according to your geographical location and language preferences.
Google emphasizes its commitment to user privacy, stating that it never shares this data without explicit notification and user consent. Furthermore, Google provides a dedicated feature, aptly named “App permissions”, which allows you to comprehensively review all applications connected to your Google Account and manage their access privileges.
In this guide, we will delve into the process of identifying which applications, websites, and online services are currently linked to your Google Account and possess access to your data. Crucially, we will also provide step-by-step instructions on how to revoke access should you deem it necessary, empowering you to maintain control over your Google Account security and privacy.
Discovering Apps Connected to Your Google Account¶
Over time, the landscape of applications and online services you utilize evolves. Some apps may become obsolete, falling out of regular use, while others may simply no longer align with your needs or preferences. Maintaining connections with dormant or unnecessary applications can pose potential security and privacy risks. It’s prudent to periodically review these connections and disconnect or remove applications that are no longer actively used or trusted.
Why is disconnecting unused apps a recommended security practice? Even when you are not actively engaging with an application, it may still retain access to your Google Account and its associated data. Consider a workout scheduling application downloaded on your smartphone that initially requested access to your Google Account for seamless integration.
This application, even in periods of inactivity, might access your Google Contacts to suggest potential workout partners based on your existing network. Alternatively, it could scan your Google Calendar to identify mutually available time slots for scheduling workout sessions with friends. While such features may have been initially appealing, if they are no longer relevant or you have concerns about data access, disconnecting the application is a sensible step.
To identify the applications that currently have access to your Google Account, navigate to the following web address in your browser: https://security.google.com/settings/security/permissions?pli=1.
Ensure you are logged in with the specific Google Account you wish to examine. Upon accessing this page, you will be presented with a comprehensive list detailing all applications and services that have been granted access to your account. Refer to the screenshot below for a visual representation of this interface.
This list is categorized to provide clarity, displaying connected and permitted devices, applications and games, web applications and websites, as well as browser extensions. To gain a deeper understanding of an individual application’s access privileges, simply click on its entry within the list. This action will reveal detailed information regarding the specific aspects of your Google Account that the application is authorized to access.
Understanding App Access Details¶
Clicking on an application in the list will expand to show you more granular details about its permissions. This is crucial for understanding the level of access you’ve granted. Pay attention to the types of data the app can access, such as:
- Contacts: Permission to view, edit, download, and manage your Google Contacts.
- Calendar: Access to view, create, modify, and delete events in your Google Calendar.
- Drive: Ability to view, manage, and potentially delete files and folders in your Google Drive.
- Gmail: Permission to read, send, delete, and manage your emails.
- YouTube: Access to your YouTube activity, watch history, subscriptions, and potentially your channel.
- Location: Permission to track your location history if location services are enabled.
The level of access varies significantly between applications. Some may only require basic profile information (name, email), while others request broader permissions to integrate deeply with your Google services. Carefully review the requested permissions before granting access to any application in the future, and periodically review the permissions of existing connected apps.
Revoking Access to Your Google Account¶
It’s important to remember that while Google facilitates the sign-in process, it does not actively review or endorse third-party websites and applications that request access to your Google Account. Google explicitly states that it assumes no responsibility for the security practices or trustworthiness of these external sites. Therefore, exercising caution and diligence in managing application access is paramount.
If you harbor any reservations or doubts regarding the legitimacy or security of a website or application requesting access to your Google Account information, the most prudent course of action is to decline the access request altogether. However, if you have previously granted access and subsequently developed concerns, or simply wish to disconnect an application you no longer use, revoking access is a straightforward process.
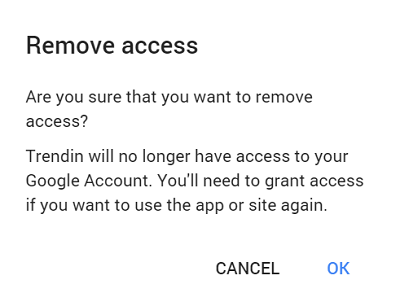
To revoke an application’s access to your Google Account, locate the application within the list of connected apps (as described in the previous section). Click on the application to view its details. Within the application’s details, you will find a “Remove Access” button, typically displayed prominently. Click this button to initiate the revocation process.
Upon clicking “Remove Access,” a confirmation prompt will appear, seeking your explicit confirmation of the action. Carefully review the prompt to ensure you are revoking access for the intended application. To proceed with the revocation, click “OK” within the confirmation prompt.
Following confirmation, you will have successfully removed the application’s access to your Google Account. The application will no longer be able to access your Google Account data, and you may need to use alternative login methods if you wish to continue using the application in the future.
It’s worth noting that revoking access prevents future access. Depending on the application and its data handling practices, some data may have already been stored or processed by the application while it had authorized access. Reviewing the application’s privacy policy can provide more insight into their data handling practices.
Regularly Audit App Permissions¶
It is a best practice to periodically audit the applications connected to your Google Account. Setting a recurring reminder to review your app permissions every few months can significantly enhance your online security and privacy posture. As your online activity evolves and you try new applications and services, your access permissions should be reviewed and updated accordingly.
This regular audit allows you to:
- Identify and remove unused or forgotten apps: Reduce the attack surface by disconnecting apps you no longer use.
- Reassess permissions of actively used apps: Ensure you are still comfortable with the level of access granted to apps you continue to use. Permissions requirements might change over time with app updates.
- Discover potentially risky apps: During your review, you might identify apps that request excessive permissions or that you no longer trust.
- Maintain control over your data: Proactively manage which applications have access to your personal information within your Google Account.
By adopting a proactive approach to managing your Google Account app permissions, you take a significant step in safeguarding your digital privacy and security.
Is it Safe to Allow Apps to Access Your Google Account?¶
The question of whether it’s safe to grant applications access to your Google Account is nuanced and depends heavily on the specific application and the level of access requested. There isn’t a simple “yes” or “no” answer, as the safety and security implications vary significantly.
When considering granting access, it’s crucial to understand the scope of access you are granting. Some applications legitimately require access to certain data to function correctly and provide their intended services. For instance, a calendar application naturally needs access to your Google Calendar to schedule events and reminders. Similarly, a photo editing application might require access to Google Photos to allow you to edit your images directly.
However, it’s essential to differentiate between necessary access and excessive or unwarranted access. An application requesting access to your Gmail inbox when its core functionality has no apparent connection to email communication should raise a red flag. Similarly, an application requesting access to your location data when location services are not relevant to its features warrants careful consideration.
Before granting access to any application, consider the following:
- Application legitimacy and reputation: Research the application developer or company. Are they reputable and trustworthy? Read reviews and check for security audits or certifications.
- Purpose of access: Clearly understand why the application needs access to your Google Account. Does the requested access align with the application’s functionality?
- Level of access requested: Review the specific permissions being requested. Is the application asking for broad access or only specific data points necessary for its operation?
- Privacy policy: Carefully read the application’s privacy policy to understand how they collect, use, and store your data.
- Alternatives: Are there alternative applications that offer similar functionality but require less access to your personal data?
When is it generally safer to grant access?
- Reputable and well-known applications: Applications from established and trusted companies with a proven track record of security and privacy are generally lower risk.
- Applications with clear and legitimate reasons for access: Applications where the requested access is directly related to their core functionality and enhances the user experience.
- Applications requesting minimal necessary access: Applications that only request the specific permissions needed to function, rather than broad or excessive access.
When should you be cautious or avoid granting access?
- Unknown or suspicious applications: Applications from unknown developers or with limited information available online should be approached with caution.
- Applications requesting excessive or unexplained access: Applications that request permissions that seem unrelated to their functionality or ask for broad access to sensitive data.
- Applications with vague or unclear privacy policies: Applications with poorly written or ambiguous privacy policies, or those that do not have a publicly available privacy policy.
Ultimately, granting access to your Google Account requires a balanced assessment of convenience and security. Prioritize applications from reputable sources, carefully review requested permissions, and always err on the side of caution when dealing with unknown or suspicious applications. Regularly reviewing and managing your app permissions is a vital step in maintaining your online security and protecting your personal data.
If you have any further questions or concerns regarding managing your Google Account privacy and app permissions, please feel free to leave a comment below. Your insights and experiences are valuable to our community.
Post a Comment